5. How secure are router ACLs
5.1. Introduction
Cisco states in
http://www.cisco.com/c/en/us/support/docs/ip/access-lists/13608-21.html
"Devised to prevent unauthorized direct communication to network devices, infrastructure access control lists (iACLs) are one of the most critical security controls that can be implemented in networks."
But how effective are those ACLs?
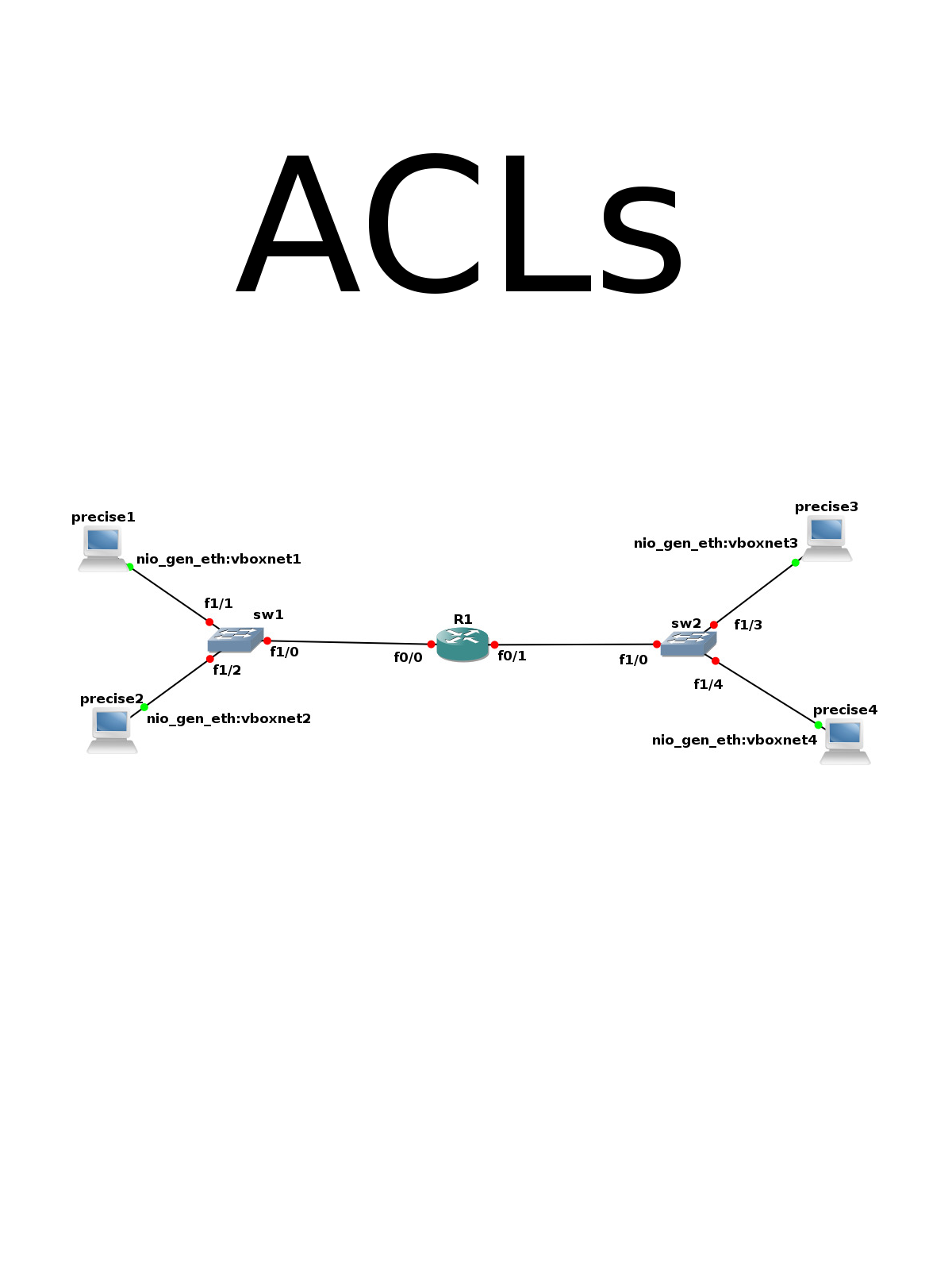
To see how effectiv the ACLs are, we introduce another host, Kali. This is a virtual machine with Kali linux which has
an eth1 adapter on vboxnet0. This virtual machine is not provisioned by Vagrant, so we'll need to do some manual
configuration:
ifconfig eth1 10.128.1.10 netmask 255.255.255.0 route add -net 10.128.0.0 netmask 255.255.0.0 gw 10.128.1.1
This is more or less the same as for precise1 and precise2.
And, because it is on sw1, we can ping precise1:
ping 10.128.1.101 PING 10.128.1.101 (10.128.1.101) 56(84) bytes of data. 64 bytes from 10.128.1.101: icmp_seq=1 ttl=64 time=1.38 ms 64 bytes from 10.128.1.101: icmp_seq=2 ttl=64 time=0.916 ms 64 bytes from 10.128.1.101: icmp_seq=3 ttl=64 time=0.910 ms ^C --- 10.128.1.101 ping statistics --- 3 packets transmitted, 3 received, 0% packet loss, time 2003ms rtt min/avg/max/mdev = 0.910/1.069/1.381/0.220 ms
5.2. Ping
But pinging the router from Kali must fail (we did not permit incoming ICMPs):
ping 10.128.1.1 PING 10.128.1.1 (10.128.1.1) 56(84) bytes of data. From 10.128.1.1 icmp_seq=1 Packet filtered From 10.128.1.1 icmp_seq=2 Packet filtered From 10.128.1.1 icmp_seq=3 Packet filtered ^C --- 10.128.1.1 ping statistics --- 3 packets transmitted, 0 received, +3 errors, 100% packet loss, time 2009ms
What is interesting is that we see that ping actually sees that the router is there (otherwise we would
get a "destination host unreachable")
The image below shows what happens. First a ping from Kali to 10.128.1.2 (a non-existing address), then
a ping to 10.128.1.1 (the router).

The ping to the non-existing address does not pass the arp-phase.
However, for the 10.128.1.1, the router replies to the ARP. Furthermore, the router replies with
an ICMP 70 (Destination unreachable).
5.3. What is behind the router?
Ping is nice, but anything behind the router is invissible for the pings. The
router effectively hides the network behind the router. The response for precise3 is the same
as for 10.128.2.109 (a non-existing host).
Of course, no-one will be discouraged by this. Nmap is always availabe on Kali:
nmap -sA 10.128.2.0/24 Starting Nmap 7.25BETA2 ( https://nmap.org ) at 2016-12-30 12:12 EST Nmap scan report for 10.128.2.1 Host is up (0.078s latency). All 1000 scanned ports on 10.128.2.1 are unfiltered Nmap scan report for 10.128.2.103 Host is up (0.26s latency). All 1000 scanned ports on 10.128.2.103 are unfiltered Nmap scan report for 10.128.2.104 Host is up (0.15s latency). All 1000 scanned ports on 10.128.2.104 are unfiltered Nmap done: 256 IP addresses (3 hosts up) scanned in 95.53 seconds
How is that possible? Wireshark shows the way this works:

We opened-up the return traffic rather wide: all established traffic is let through. You can ofcourse
limit this traffic by allowing only specific return traffic. This effictively doubles the size of
your access-list. That means that you will make a trade-off between manegeability and security.
It may also be a good idea to get a firm control of any trafic that leaves the router. The
recomendation to place extended ACLs close to the source is therefore perhaps not such a good
idea.
However, the router is still a stateless inspection device. Each packet is examined individually; no mechanism
exists to relate a packet to an existing session. This, in addition to the fact that router ACLs are
not really easily managed, introduces the need for a more sophisticated device, the firewall.