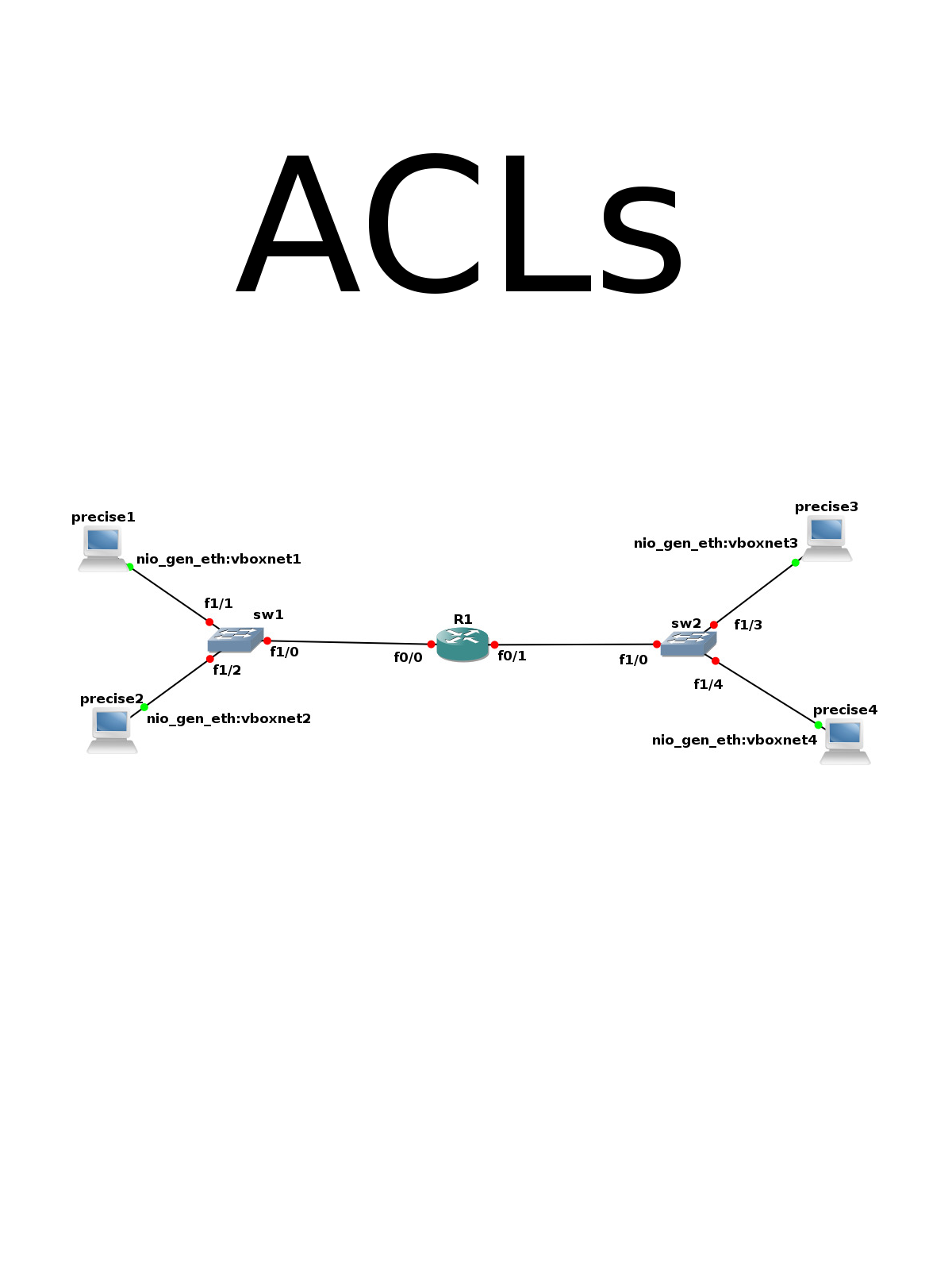
4. Example ACLs
4.1. A standard ACL
In our test network, we will allow precise1 to access the precise3 and 4, but we will disallow precise2 that access.
source
|
destination
|
action
|
precise1
|
precise3, precise4
|
allow
|
precise2
|
precise3, precise4
|
deny
|
Because this is just a simple exersice, we will not place any filters for the return traffic.
The ACL becomes:
access-list 1 permit 10.128.1.101 access-list 1 deny 10.128.1.102
And we will apply it to interface f0/0 incoming:
interface FastEthernet0/0 ip access-group 1 in
To test, a simple ping will do; standard ACLs do not use protocol or port filtering.
[ljm@verlaine acl]$ vagrant ssh precise1 -c 'ping -c1 10.128.2.103' PING 10.128.2.103 (10.128.2.103) 56(84) bytes of data. 64 bytes from 10.128.2.103: icmp_req=1 ttl=63 time=13.6 ms --- 10.128.2.103 ping statistics --- 1 packets transmitted, 1 received, 0% packet loss, time 0ms rtt min/avg/max/mdev = 13.672/13.672/13.672/0.000 ms Connection to 127.0.0.1 closed. [ljm@verlaine acl]$ vagrant ssh precise2 -c 'ping -c1 10.128.2.103' PING 10.128.2.103 (10.128.2.103) 56(84) bytes of data. From 10.128.1.1 icmp_seq=1 Packet filtered --- 10.128.2.103 ping statistics --- 1 packets transmitted, 0 received, +1 errors, 100% packet loss, time 0ms Connection to 127.0.0.1 closed. [ljm@verlaine acl]$
Removing the ACL is done with the
no
keyword:
r1#conf t Enter configuration commands, one per line. End with CNTL/Z. r1(config)#int f0/0 r1(config-if)#no ip access-group 1 in r1(config-if)#^Z r1#conf t r1(config)#no access-list 1 r1(config)#^Z r1#
And a verification that the access-list is now gone:
[ljm@verlaine acl]$ vagrant ssh precise1 -c 'ping -c1 10.128.2.103' PING 10.128.2.103 (10.128.2.103) 56(84) bytes of data. 64 bytes from 10.128.2.103: icmp_req=1 ttl=63 time=33.8 ms --- 10.128.2.103 ping statistics --- 1 packets transmitted, 1 received, 0% packet loss, time 0ms rtt min/avg/max/mdev = 33.857/33.857/33.857/0.000 ms Connection to 127.0.0.1 closed. [ljm@verlaine acl]$ vagrant ssh precise2 -c 'ping -c1 10.128.2.103' PING 10.128.2.103 (10.128.2.103) 56(84) bytes of data. 64 bytes from 10.128.2.103: icmp_req=1 ttl=63 time=28.8 ms --- 10.128.2.103 ping statistics --- 1 packets transmitted, 1 received, 0% packet loss, time 0ms rtt min/avg/max/mdev = 28.880/28.880/28.880/0.000 ms Connection to 127.0.0.1 closed. [ljm@verlaine acl]$
4.2. Extended numbered
Extended numbered ACLs offer greater flexibility. To show this, we will allow the following
trafic:
source
|
destination
|
port
|
action
|
precise1
|
precise3
|
tcp
901,tcp
902
|
allow
|
precise1
|
precise4
|
tcp
903,tcp
904
|
allow
|
precise2
|
precise3
|
tcp
905,tcp
906
|
allow
|
precise2
|
precise3
|
tcp
907,tcp
908
|
allow
|
precise3
|
precise1,precise2
|
tcp_909
|
allow
|
This table sees the router as a single filtering component between the two networks. But that is
not the way that a router works. There will be differnt ACLs, based on the direction of the
traffic. Also, we need to consiider on which interface the ACLs are placed. Cisco recommends:
-
place extended ACLs close to the source
-
place standard ACLs close to the destination But that guideline does not look at the fact that you may have a loopback address available in your router.
We'll define two ACLs, one from 10.128.1.0/24 to 10.128.2.0/24 and one the otherway around:
access-list 110 permit tcp host 10.128.1.101 host 10.128.2.103 eq 901 access-list 110 permit tcp host 10.128.1.101 host 10.128.2.103 eq 902 access-list 110 permit tcp host 10.128.1.101 host 10.128.2.104 eq 903 access-list 110 permit tcp host 10.128.1.101 host 10.128.2.104 eq 904 access-list 110 permit tcp host 10.128.1.102 host 10.128.2.103 eq 905 access-list 110 permit tcp host 10.128.1.102 host 10.128.2.103 eq 906 access-list 110 permit tcp host 10.128.1.102 host 10.128.2.104 eq 907 access-list 110 permit tcp host 10.128.1.102 host 10.128.2.104 eq 908 access-list 110 permit tcp any any established access-list 111 permit tcp host 10.128.2.103 host 10.128.1.101 eq 909 access-list 111 permit tcp host 10.128.2.103 host 10.128.1.102 eq 909 access-list 111 permit tcp any any established
Any traffic that has the 'established'-bit set is allowed. This allows return-traffic
in an existing session to pass through the router.
The access-list 110 is put on f0/0 as input list and 111 on f0/1 as input.
int f0/0 ip access-group 110 in int f0/1 ip access-group 111 in
Verifying gives:
vagrant ssh precise1 -c 'telnet 10.128.2.103 901' Trying 10.128.2.103... Connected to 10.128.2.103. Escape character is '^]'. /root/s901 Connection closed by foreign host. Connection to 127.0.0.1 closed. [ljm@verlaine acl]$ vagrant ssh precise1 -c 'telnet 10.128.2.103 902' Trying 10.128.2.103... Connected to 10.128.2.103. Escape character is '^]'. /root/s902 Connection closed by foreign host. Connection to 127.0.0.1 closed. [ljm@verlaine acl]$ vagrant ssh precise1 -c 'telnet 10.128.2.103 903' Trying 10.128.2.103... telnet: Unable to connect to remote host: No route to host Connection to 127.0.0.1 closed. vagrant ssh precise3 -c 'telnet 10.128.1.101 909' Trying 10.128.1.101... Connected to 10.128.1.101. Escape character is '^]'. /root/s909 Connection closed by foreign host. Connection to 127.0.0.1 closed. [ljm@verlaine acl]$ vagrant ssh precise3 -c 'telnet 10.128.1.101 908' Trying 10.128.1.101... telnet: Unable to connect to remote host: No route to host Connection to 127.0.0.1 closed.
The rest is also as expected.