3. ACL Basics
3.1. Introduction
Cisco uses ACLs to filter traffic. ACLs are also used in different contexts, like
for example NAT. Access lists consist of a number of permit and deny rules.
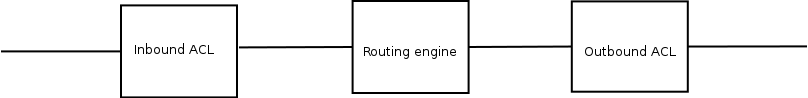
ACLs are placed on an interface and there are inbound and outbound ACLs.
People tend to view a router with ACLs as a sort of firewall thing. The main difference
is that a router in general does not do statefull filtering. If statefull filtering is
used (Cisco calls it reflexive), it consumes a lot of resources on the router.
There are two types of ACL:
-
standard: deny from source IP addresses
-
extended: allow more criteria, like port numbers, destination and protocol
ACLs are numbered:
standard
|
1-99
|
1300-1999
|
extended
|
100-199
|
2000-2699
|
In general, you will make a design based on what you wantt to filter, where and why. Before
you do however, you need to know the properties of the filtering and the options.
It is exactly this what we want to do here.
The simpler filter ACLs are, the better. Although routers can be re-configured
from time to time, in general the management tooling is not made for frequent
rule changes (like in firewalls).
3.2. ACL types
Filtering ACLs are connected to an interface.
ACLs that are used for filtering can be
-
inbound
-
outbound
There are two types of ACL:
-
standard: deny from source IP addresses
-
extended: allow more criteria, like port numbers, destination and protocol
ACLs are named or they are numbered:
standard
|
1-99
|
1300-1999
|
extended
|
100-199
|
2000-2699
|
Standard ACLs are much more simple than extended. Standard ACLs only allow filtering of
source IP. The following table gives the idea behind ACLs:
type:
|
numbered
|
named
|
|
ID:
|
number
|
name
|
|
configure with
|
global commands
|
sub commands
|
|
standard numbered |
standard named |
standard matching: source IP address |
|
extended numbered |
extended named |
extended matching: source & dest. IP source & dest. port other criteria |
In general, the most ACLs that I have seen are extended numbered.
ACLs are followed top-to-bottom; the first matching rule defines the action.
3.3. Creating ACLs
3.3.1. Standard numbered
Matching a single IP address:
access-list 1 permit 10.128.1.101
Matching a subnet is a bit counter-intuitive. Cisco has chosen to create a "wildcard mask" for this,
in stead of using the normal subnet mask. Mainly to annoy people, I presume. The wildcard mask is the
inverse of the subnet mask, for all practical purposes.
An example then would be:
access-list 2 permit 10.128.2.0 0.0.0.255
3.3.2. Extended numbered
Extended ACLs allow a finer control of the filtering. The syntax is:
access-list <number> {permit|deny} <protocol> <source> <destination> [port specification] [other options]
parameter
|
explanation
|
access-list
|
the keyword to define the accesslist
|
number
|
the number of the ACL; 100-199 or 2000-2699 for extended ACLs
|
permit|deny
|
allow or deny ation for this rule
|
protocol
|
name of the IP protocol. Usually ip, tcp, udp or icmp.
|
source
|
can be a single host or an subnet with wildcard mask
|
destination
|
can be a single host or an subnet with wildcard mask
|
port specification
|
an operator (lt (less than), gt (greater than), eq (equal), ne (not equal) or range) with e port specification.
|
other options
|
mostly used to specify 'established' to allow only one direction of the traffic.
|
The source and destination can be:
any
|
the any keyword matches any ip address
|
host |
the host-keyword, followed by an IP address matches a single host
|
matches a subnet; the wildcard mask has been described above.
|
3.3.3. Named ACLs
Although named ACLs should provide some more documentational advantages, I have seldom seen them being
used. The definition is a bit different, but the concepts are more or less the same.
ip access-list standard filtername permit 10.128.1.101 permit 10.128.1.102
Likewise, extended ACLs can be created. Functionally, the named ACLs are the same as their numbered cousins.
Therefore, we'l not continue with these named ACLs.