Changing Distributions
|

|
8. Salix on Luks
8.1. Intro
If you have a laptop that you take with you some of the time, you will want
harddisk encryption. On Linux systems, that can be done with LUKS. However,
the installation process of Salix does not offer these facilities. Furthermore,
the installation process is simplified, so it is
not that easy to insert specific
steps.
First of all, it is assumed that you have a Salix install image, so
I won't go into the download of Salix. Second, you need a computer
to test with. I first tested this on a virtualbox, and it is a wise
approah to test is before disabeling all your computers.
8.2. Installation
After the boot, you will get some screens that ask for keymaps etc.
Then you get:

Select "Exit installation" here. You will be greeted with a prompt.
8.2.1. Partitioning the disk
First we will be partitioning the harddrive in two partitions:
In my virtualbox set-up, the installable disk is /dev/sda and at the beginning
it is completely empty.
Start
fdisk /dev/sda
and type:
-
n (for a new partition)
-
p (for a primary partition)
-
1 (the first)
-
press enter for the default first sector
-
+500M to create a partition of 500M
-
a (to make the partition bootable)
-
n to make the second partition
-
enter to accept all the defaults. This will create a partition for the rest of the disk.
-
w to write the partition table to the disk.
If you are paranoid, you will probably take the time to write
random bytes to your encrypted partition here. This is a good step
to keep forensics people in the dark, but it takes time, so
if you do a virtualbox test, you might skip that step.
dd if=/dev/urandom of=/dev/sda2
8.2.2. LVM and Luks
The second partition will be an encrypted volume group, with
two logical volumes, root and swap.
Now we get the partition ready for encryption:
root@salix64:/# cryptsetup -s 256 -y luksFormat /dev/sda2
WARNING!
========
This will overwrite data on /dev/sda2 irrevocably.
Are you sure? (Type uppercase yes): YES
Enter passphrase:
Verify passphrase:
root@salix64:/#
Next, we'll open the encrypted partition with:
cryptsetup luksOpen /dev/sda2 slackcrypt
This will open a partition
/dev/mapper/slackcrypt
that can be accessed as unencrypted.
On this partition, we'll create a physical volume group with:
pvcreate /dev/mapper/slackcrypt
and a volumgroup:
vgcreate cryptvg /dev/mapper/slackcrypt
And in that volumegroup a number of logical volumes:
lvcreate -L 25G -n root cryptvg
lvcreate -L 5G -n swap cryptvg
You will adjust the size to your specific situation.
The stuff we created need some nodes to find everything back:
vgscan --mknodes
vgchange -ay
And we'll created the swap-space:
mkswap /dev/cryptvg/swap
8.2.3. Install Salix
Now, we'll restart the set-up menu:
setup
In the screen for the PARTITIONS EDITOR, don't select any partitions, but
just select Go.
Setup will detect the swap-space
/dev/cryptvg/swap
so you might as well enable it.
For the root filesystem, select
/dev/cryptvg/root
because that will be your LVM root partition. Format it (I usually
format as ext4fs).
Next, add
/dev/sda1
as
/boot
because you will boot from an un-encrypted partition. Format
it. And then, select done. Your partition table will look like this.
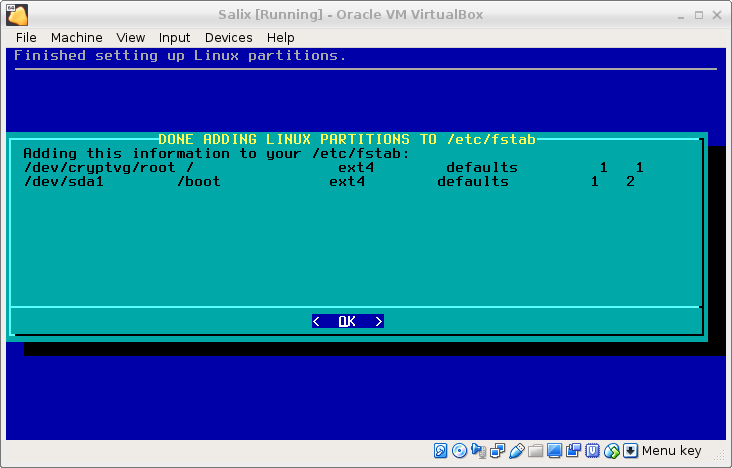
The rest of the install is the standard Salix install. Because that is
so simplified, that it won't need any explanation.
After a while, you will come to the screen
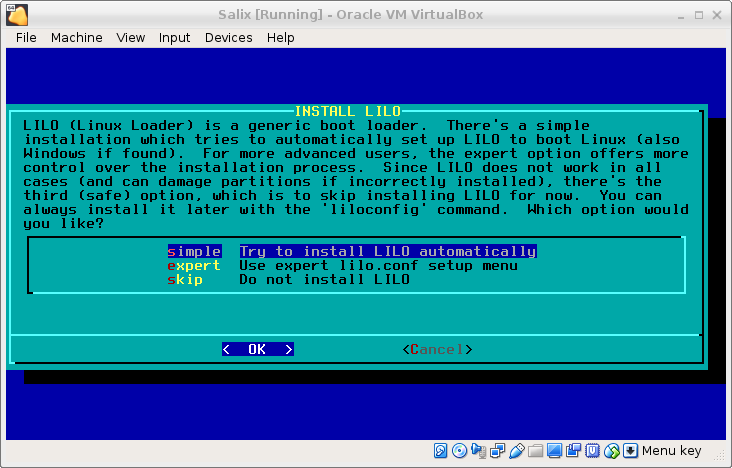
Select Expert and then Begin; accept a number of defaults, until
you get to the screen SELECT LILO TARGET LOCATTION. As target,
select MBR, select
/dev/sda
and choose your delay.
Now you have to select “Linux: Add a linux partition …” and select
/dev/cryptvg/root
to boot. (Yes,
/dev/cryptvg/root
not
/boot
) As Partition name, you might use "Salix".
Once that’s been selected, install lilo. It may throw a warning.
There are a number of additional steps in the standard installation:
-
hardware clock
-
timezone
-
numlock
-
user setup
-
etcetera
until you reach:
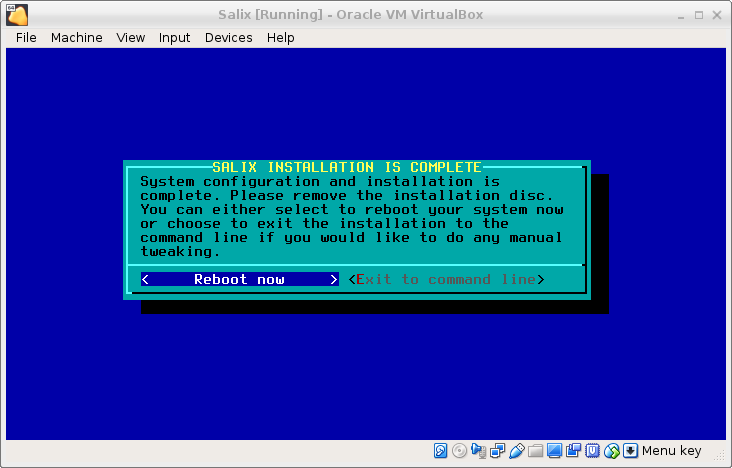
where we choose Exit to command line.
8.2.4. Fix boot
Now we have to fix lilo because of our encryption scheme.
First of all, run this:
chroot /mnt
Find out which kernel you are installing with
ls /lib/modules
It will be someting like 3.10.17 or 4.4.14. Next type:
mkinitrd -c -k *insert kernel number* -m *insert ROOT file system type
here* -f *insert root file system type here* -r /dev/cryptvg/root -C
/dev/sdx2 -L
For me (Salix 14.2), that was:
mkinitrd -c -k 4.4.19 -m ext4 -f ext4 -r /dev/cryptvg/root -C /dev/sda2 -h /dev/cryptvg/swap -L
The -h should allow hybernation.
Edit Lilo's config-file
vi /etc/lilo.conf
and make the image-section look like:
image = /boot/vmlinuz
initrd = /boot/initrd.gz
root = /dev/cryptvg/root
label = Salix
read-only
append = "vt.default_utf8=0 resume=/dev/cryptvg/swap"
Check with
ls /boot
if the image and initrd are there. Run
lilo
and reboot.
The boot process will throw some error messages about modules that cannot
be loaded. I'm working on how they should be solved. But the boot process
will ask for the passphrase to unlock the encrypted volume, and, when the
passphase is given, it will present the system on the encrypted volume.





