2. The network
2.1. The switch
Because GNS3 does not support port security, the test needs to be done with physical hardware.
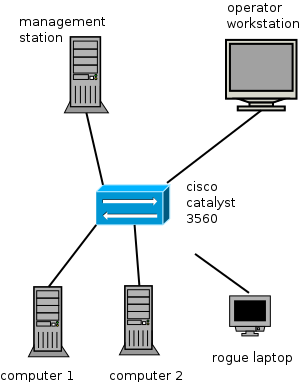
The switch is a Cisco Catalyst 3560 with IOS 12.2, because that is what I got. most cisco switches will support port security, so it doesn't really matter. The switch has a DHCP server and all ports are assigned to VLAN 10. Syslog is redirected to the management server
The most relevant parts of the general config are:
ip dhcp excluded-address 192.168.10.1 192.168.10.10 ip dhcp excluded-address 192.168.10.51 192.168.10.255 ! ip dhcp pool CLIENT network 192.168.10.0 255.255.255.0 ! spanning-tree mode pvst spanning-tree portfast default spanning-tree extend system-id vlan 10 ! interface Vlan10 ip address 192.168.10.1 255.255.255.0 ! logging 192.168.10.2
2.2. The management server
The management server is a raspberry pi. Besides the reception of syslog, it is used to launch scripts that automate the tedious cisco command line use.
The pi uses rsyslogd. Standard, it does not receive syslog from other servers. In /etc/rsyslog.conf you need to add:
$ModLoad imudp $UDPServerRun 514 # provides TCP syslog reception $ModLoad imtcp $InputTCPServerRun 514
In the catch-all section, I added local7 to /var/log/messages because cisco logs on local7:
*.=info;*.=notice;*.=warn;\ auth,authpriv.none;\ cron,daemon.none;\ local7.*;\ mail,news.none -/var/log/messages
2.3. The rest
For computer1 and computer2, you can use anything that has an ethernet NIC. The admin workstation needs to be able to ssh into the pi.
