2. Installing a DHCP server
2.1. Installing the software
We'll use xenial1 as our DHCP server. Installing is default:
apt-get install dhcpd
This makes the setup for xenial1 as follows:
#!/bin/bash ETH1=$(dmesg | grep -i 'renamed from eth1' | sed -n 's/: renamed from eth1//;s/.* //p') ifconfig $ETH1 down ip link set $ETH1 name eth1 ifconfig eth1 10.168.65.101 netmask 255.255.255.0 up route add -net 10.168.0.0 netmask 255.255.0.0 gw 10.168.65.1 apt-get install dhcpd cp /vagrant/udhcpd.conf /etc cp /vagrant/udhcpd.default /etc/default/udhcpd /etc/init.d/udhcpd restart
2.2. Configuration
The setup-script copies a configuration from our
/vagrant
directory. The content of
udhcpd.conf
is:
# Sample udhcpd configuration file (/etc/udhcpd.conf) # The start and end of the IP lease block start 10.168.65.200 end 10.168.65.250 interface eth1 static_lease 02:00:00:00:00:02 10.168.65.55 static_lease 02:00:00:00:00:03 10.168.63.222 option subnet 255.255.255.0 opt router 10.168.63.1 option lease 30
We see the
static_lease
for the MAC-IDs that we defined in our vagrant file. We also see that the router is defined as
10.168.63.1. We're not really interested in routing here, and because xenial1 is here the
center of our universe, we're only interested in getting traffic to xenial1. We do not care that this
router information is invalid for xenial2.
The lease time is short, because I do not want to wait long wth wireshark.
2.3. A simple network for DHCP testing
In GNS3, I created the following network.
Precise1 is on vboxnet1; xenial2 is on vboxnet2.
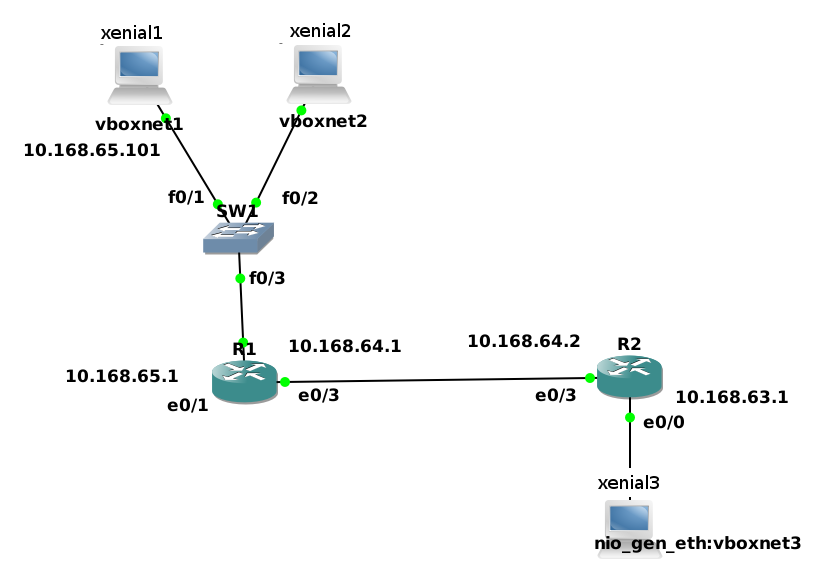
The switch is a standard GNS3-switch.
When xenial2 is started, it generates dhcp requests. This is directly visible
on the console as a series of
Sending OFFER
and
Sending ACK
with the IP address.
# pkill udhcp # # udhcpd -f udhcpd (v1.18.5) started udhcpd: max_leases=235 is too big, setting to 51 Sending OFFER of 10.168.65.55 Sending OFFER of 10.168.65.55 Sending ACK to 10.168.65.55 Sending ACK to 10.168.65.55 Sending ACK to 10.168.65.55 Sending ACK to 10.168.65.55
An
ifconfig eth1
on xenial2 will show that the predicted IP address is present on that interface.
